In a digital landscape where data breaches and cyber threats are at every corner, the importance of robust cybersecurity practices has never been more important. Today, I will show you how I captured a password using Wiresahrk, a powerful and widely-used network analysis tool. Wireshark, is an open-source packet analyzer that allows us to capture and dissect network traffic, providing valuable insights into the communication occurring within a network. By capturing and analyzing packets in real-time, Wireshark allows us to see a hidden world of data exchanges, offering us a glimpse into the inner workings of network protocols and their vulnerabilities. As I walk you through this experience capturing a cleartext password in a testing environment, we’ll explore the fascinating capabilities of Wireshark.
One of the key factors contributing to the successful capture of the password in this scenario was the use of an HTML-based website, which, by today’s security standards, is considered less secure. HTML, or Hypertext Markup Language, is the backbone of most web pages, providing the structure and layout for displaying content. However, HTML alone lacks the sufficient security measures required to protect sensitive user information. Unlike modern web frameworks and protocols that employ strong encryption methods (HTTPS), HTML-based websites often transmit data, including passwords, in cleartext format. As a result, any network packet capturing tool, such as Wireshark, can intercept and expose these unencrypted transmissions. This serves as a reminder of the importance of adopting secure web development practices, including the use of HTTPS, encryption algorithms, and secure authentication mechanisms, to keep user credentials safe from prying eyes in an increasingly hostile digital landscape.
Let’s get into the tutorial. We will be using Kali Linux since it comes with Wireshark preinstalled.

First lets make sure tcpdump is installed. Run this command: sudo apt install tcpdump

Lets run ifconfig to see what adapter we will want to capture traffic on. Here we see that it will be eth0.
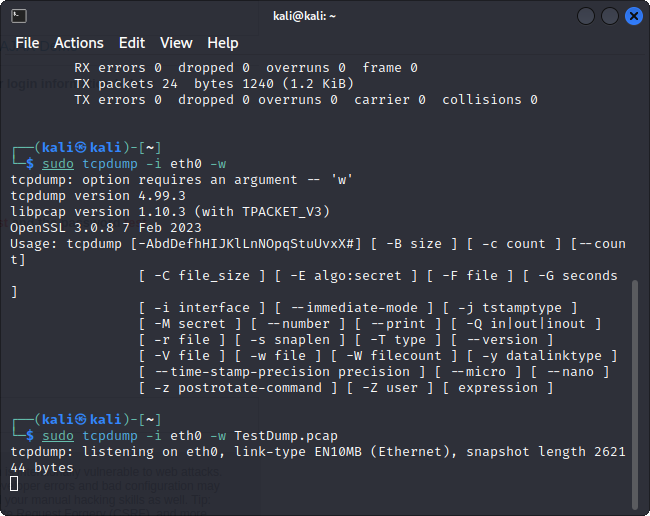
Type: sudo tcpdump -i eth0 -w TestDump.pcap
This command will allow us to listen on eth0, the adapter we identified before this step.

We will be going to vulnweb.com/login-php, its a website that is intentionally vulnerable so that we can test things like this. Here you can see a login field like you would see on any normal site.

Here we will come up with any random credentials you want. Click login when you are done.
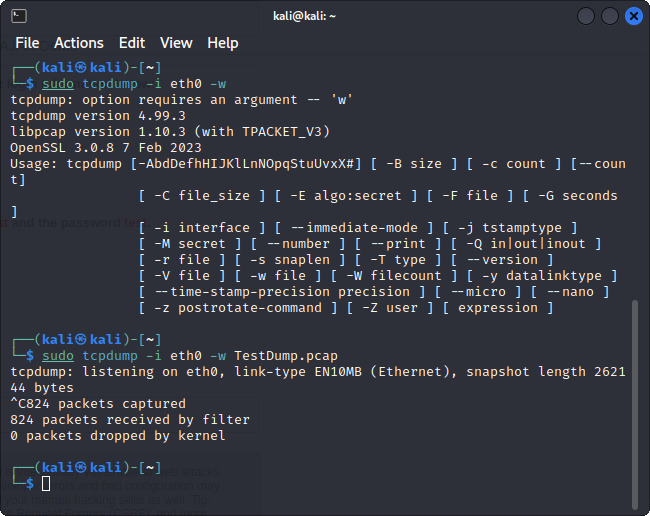
Lets go back to our terminal and press control + c on our keyboard to stop the packet capture.
After you have stopped the packet capture, type in: wireshark TestDump.pcap. If you named your pcap file something different use that name instead.
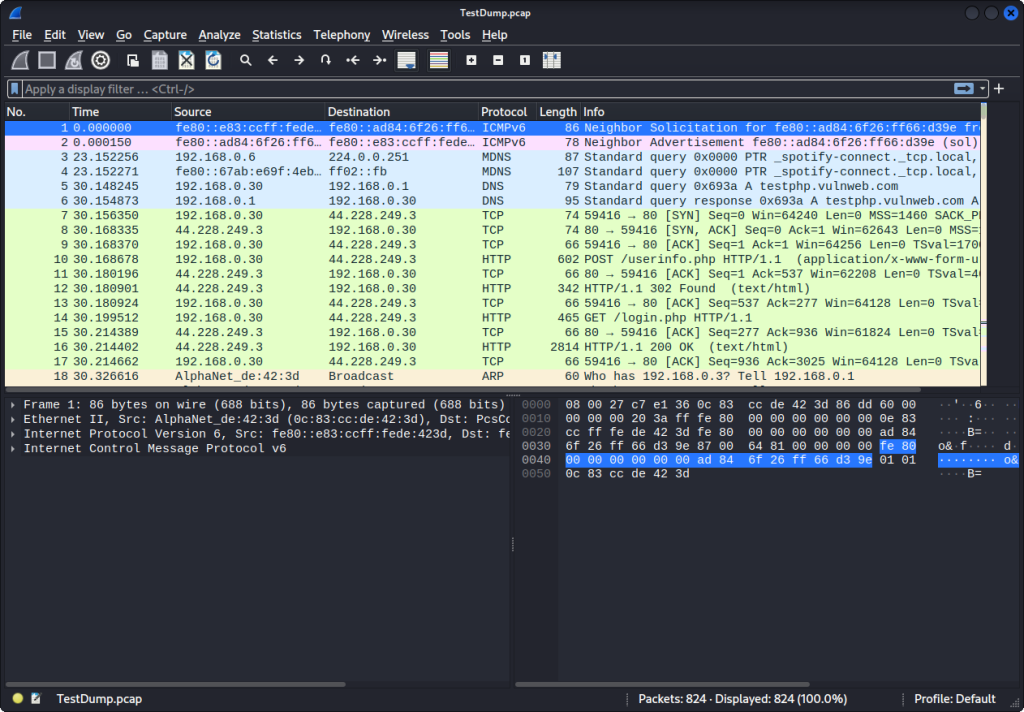
From here, the Wireshark GUI opens up. Here we can see a bunch of packets.
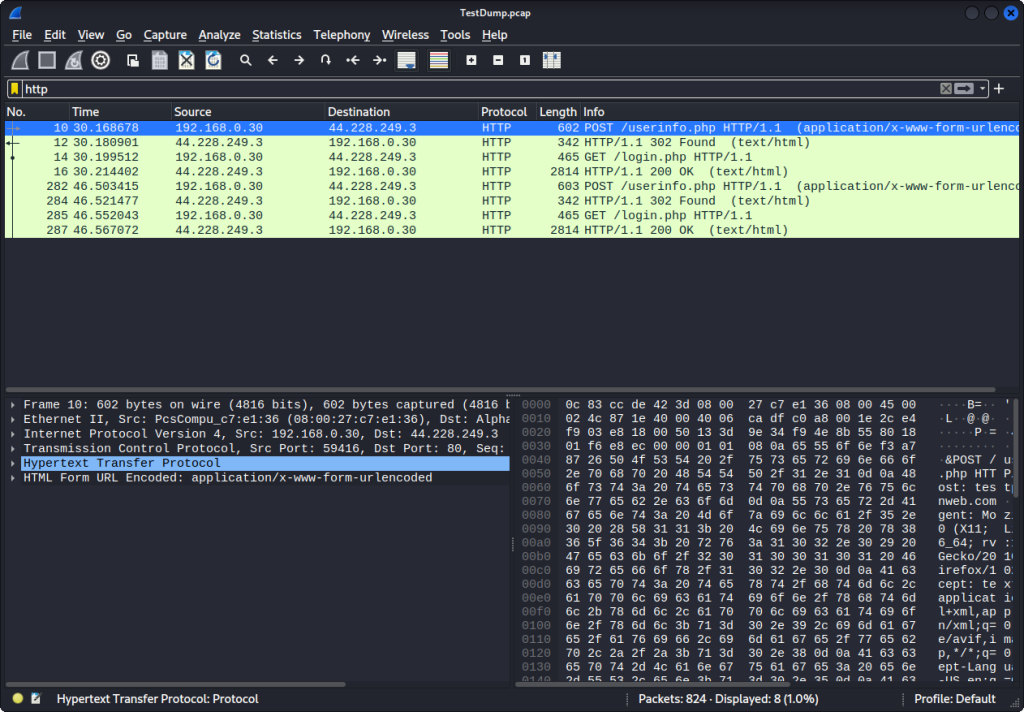
We can use filters so we don’t have to manually go through each packet. Here we filter by HTTP because we know the packet we want to look at will be HTTP. Start clicking through. You will see there are GET and POST in some of these HTTP packets. These terms refer to two different types of HTTP requests, each serving a different purpose in the communication between a client (typically a web browser) and a server.
GET Requests: GET is an HTTP method used to retrieve data from a server. When a client sends a GET request to a server, it is asking for a specific resource or information to be returned. This could be a web page, an image, a document, or any other content hosted on the server. GET requests are generally used when a client wants to retrieve data without making any changes or modifications on the server.
POST Requests: POST is another HTTP method, but it serves a different purpose compared to GET. When a client sends a POST request to a server, it is submitting data to be processed or stored. Unlike GET requests, POST requests can contain additional data, such as form inputs, login credentials, or any other information to be transmitted to the server for processing. POST requests are commonly used when submitting forms, sending data to an API, or performing actions that involve changing server-side data.
We should be able to find our passwords in a POST Request. So lets start clicking around and looking through them.

After looking through each one, I found this one. On the bottom left, go ahead and click on HTML Form URL Encoded
From here you can see the form items below it: “uname” and “pass“
And after the = sign you can see the credentials we typed in on the vulnerable website.
This eye-opening experience serves as an important reminder of the current risks that surround us in the digital landscape. While the demonstration took place in a controlled testing environment, and with HTTP (nobody uses this anymore) it highlights the critical importance of implementing robust cybersecurity practices in real-world scenarios. Encryption, secure protocols, and user awareness are key pillars in safeguarding sensitive information from falling into the wrong hands. By using tools like Wireshark, we gain invaluable insights into the inner workings of network protocols, enabling us to identify weaknesses and improve our network defenses.