Today, I used a tool called “Nessus” which is a Vulnerability Management tool. What is Vulnerability Management? Vulnerability Management is a process that involves identifying, assessing, prioritizing, and reducing vulnerabilities in systems, networks, etc. The goal of this is to lower the chances of a security breach or attack by finding vulnerabilities before they can be exploited.


I tried restarting the VM. Didn’t work. I went online and searched for solutions. On the VMWare settings I switched the Network Adapter connection to NAT instead of Bridged. After this, I finally had Internet connectivity. But for this project I needed it to be Bridged. As you can see NAT makes the VM share the hosts IP address. So if we ran a Nessus scan while in NAT mode I’m not sure how Nessus was going to react when its trying to scan two machines who are sharing the same IP address. Or if it would even be scanning the correct machine. So I needed this to work in Bridged mode.
I continued doing research until I came upon a forum. After going through the entire forum thread, I found the fix. I had to disable all the unnecessary network adapters I had on my host machine and to only have one adapter enabled (the one that’s connecting to the internet on your host machine.) Which for us, was the NETGEAR A7000 WiFi USB3.0 Adapter. As you can see in the screenshot above, that’s the only one I left enabled.
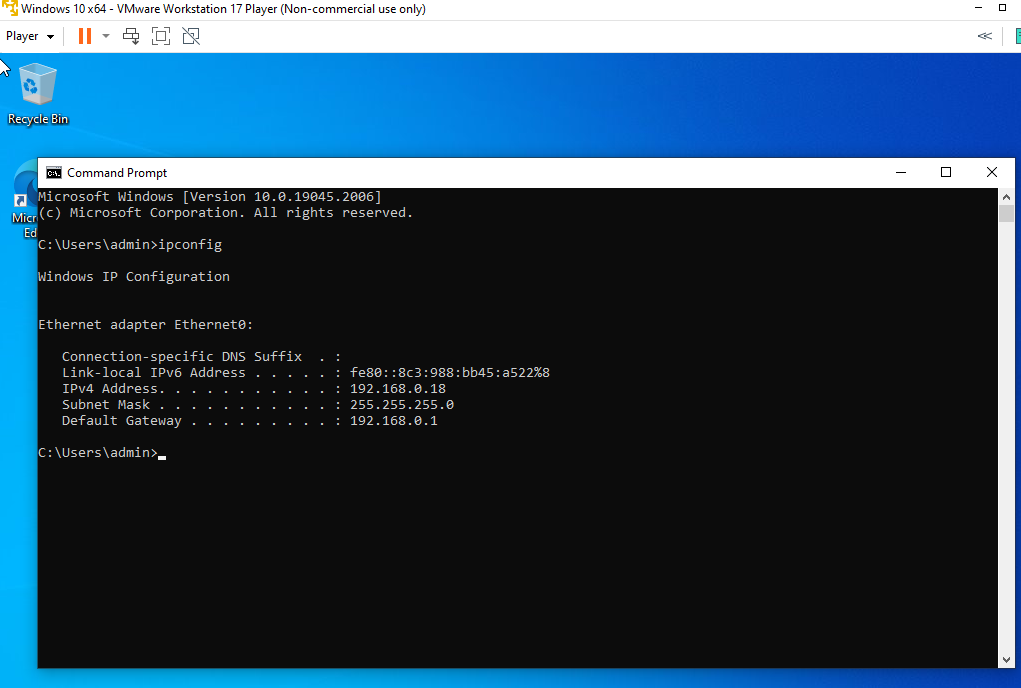

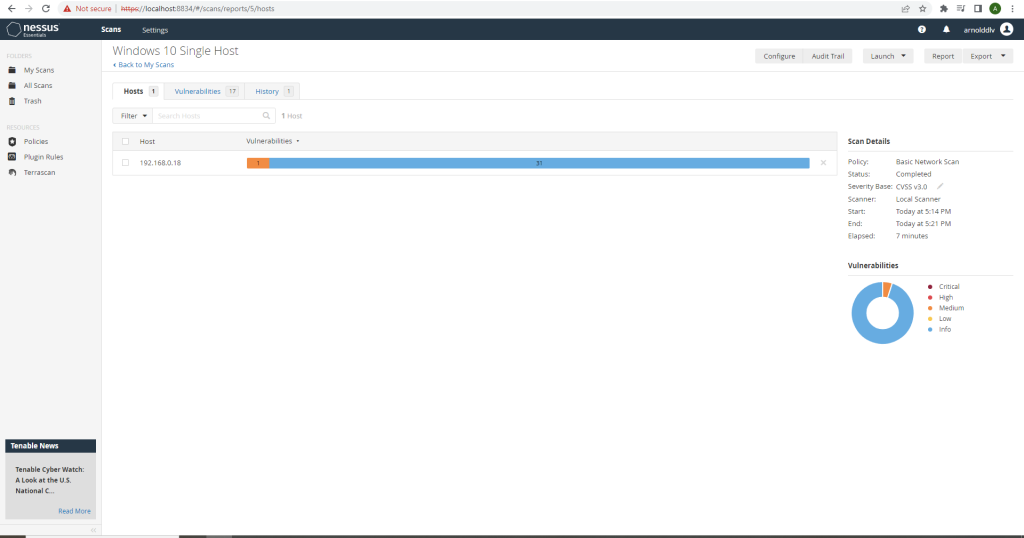



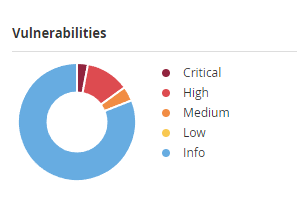
With the images above you can clearly see that the credentialed scan is able to perform a much more in-depth scan of your overall system, finding more vulnerabilities.
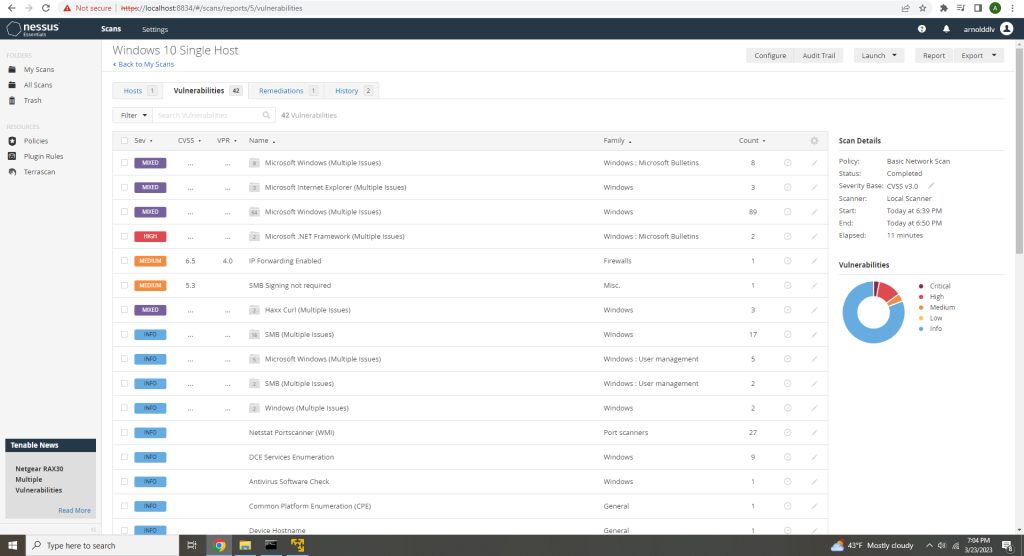
Overall, Nessus is a Vulnerability Management tool that allows you to scan machines so you can find and fix vulnerabilities before an attacker exploits them and can end up costing your company millions of dollars. Is it possible to perform this type of scan without Nessus? Yes, there’s probably other tools out there, and there’s probably ways you can do it manually. But if your organization is huge I doubt you would want your IT department going through each machine connected to your network manually.